Kismet is a wireless "detector, sniffer, and intrusion detection system," and one of the growing list of essential open source tools for computer network security professionals. Kismet runs on any POSIX-compliant platform, including Windows, Mac OS X, and BSD, but Linux is the preferred platform because it has more unencumbered RFMON-capable drivers than any of the others.
Monitor mode ability is critical to fully utilizing Kismet, because it allows Kismet to examine all the packets it can hear, not just those of whatever access point (AP) -- if any -- you are currently associated with. Almost as important to police, intelligence agencies, and black hat hackers is the fact that it allows Kismet to work passively, intercepting and collecting packets without leaving any fingerprints of its own behind.
The point is that if you want to investigate Kismet fully, the first step is to ensure that you have a driver taht supports RFMON -- monitor mode -- for your wireless network interface card (NIC). Check the Kismet links page for information on the drivers available for your brand and model NIC.
Configuration models
Kismet is designed as a client-server application, but it can be run as a standalone application, as a server supporting a number of clients, and even as a server with "drone" Kismet installations across a network, each monitoring its own wireless hardware, and all forwarding captured packets to a server. Run standalone, you simply use the built-in client. But there are also a number of third-party clients available for Kismet; if you would like to try one, visit the same page of links noted above.
Each of these components requires its own configuration file, and those files do much of the work required to get Kismet performing as you wish. They are the kismet.conf, kismet_ui.conf, and kismet_drone.conf files. The Kismet Web site contains extensive documentation on the configuration files and other things you may need to tweak.
I tried Kismet in a standalone configuration, running from the BackTrackNETGEAR RangeMax wireless PC card. Even in such a simple implementation, the configuration details can bite you. Among other things, pay careful attention to the section in the online documentation about defining your wireless cards, which Kismet documentation refers to as capture sources. The definition has to be correct or Kismet will not work at all or not work correctly. 3 distro beta, and using a single RFMON-capable NIC, a
As noted in my Backtrack 3 review, I also had to use ifconfig to disable my laptop's built-in wireless card, which like the NETGEAR RangeMax is based on the Atheros chipset, then use wlanconfig to put the NETGEAR card into monitor mode prior to starting Kismet.
Top-down UI
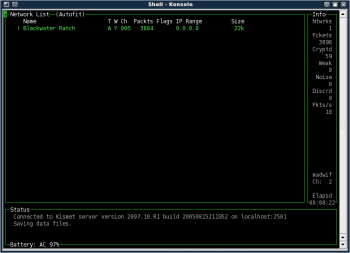
The Kismet user interface is not intuitive, but it is fast and powerful, and easy to use once you get used to it. By default, the UI opens with Autofit, a top-level list of all the networks it can see (Figure 1). From this viewpoint, you can learn basic information about the networks detected, but -- unlike other network list modes -- you can't drill-down for more detailed information.
The Autofit Network listing shows a decay indicator, network name, network type, WEP status, channel used, packets seen, flags, IP range, and the size of the capture file. The decay indicator may be an exclamation mark (!), a period (.), or a blank. An exclamation mark indicates recent activity, the period less recent activity, and blank means no recent activity. The definition of recent is based on the decay variable in kismet_ui.conf. The default decay value is three seconds.
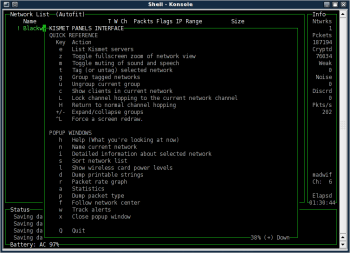
To drill down and gain more specifics, you first have to change to a different view. The Kismet interface provides a help function that explains in detail how to do this. Press h to get the help pop-up window (Figure 2). You can press x to close it or any other pop-up you may be viewing, and you can scroll through the help screens using the Page Up and Page Down keys.
If you scroll to the last screen in the help pop-up, you'll see the following in capital letters: ALL NETWORK SELECTION, TAGGING, GROUPING, SCROLLING, AND SO ON IS DISABLED IN AUTOFIT MODE. So let's change modes and see what else Kismet can tell us about the network.
After closing the help pop-up, press s to select a different sort order for the network list, then press b or B to order the list by BSSID, which is the MAC address of the network's AP. The title of the Network List panel will now read Network List (BSSID), and you can use the up or down arrow keys to scroll up and down the list to the device you're interested in learning more about.
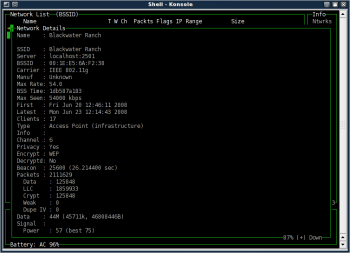
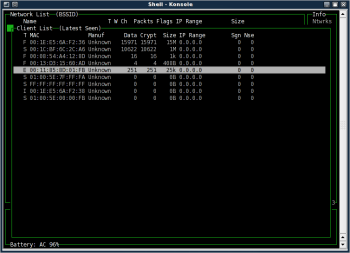
With the network of interest highlighted, press i to get complete, detailed information about that AP (Figure 3). Press a to see statistics about its traffic by channel, or press c to view the MAC addresses of all clients Kismet has detecting talking to the AP (Figure 4). If you're using Kismet to protect your own AP, that last choice will be especially interesting to you.
Note that when the client list appears after you press c, the panel window shows Client List (Autofit). It works just like the Network List, meaning that in order to drill deeper, you'll need to change the view in the same way you did before. I chose l to list the clients in latest seen order (Figure 5). A capital L would reverse that list, so that the most recently seen clients would appear at the bottom.
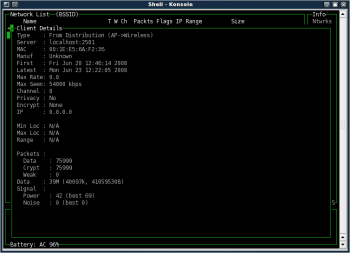
Highlight a particular client, just as you did a network, then press i to see what information about the client is available. Kismet will show you the data in Figure 6, which includes the type of connection, MAC address, and much more.
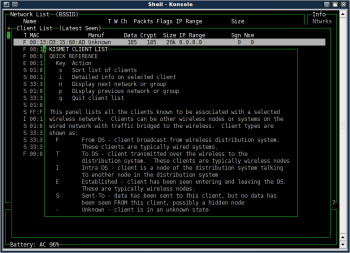
Also note that the h function now shows context-specific help, not the same help information you saw when pressing h with the default Network List displayed. In this case, most of the screen is dedicated to explaining the various connection types: From DS, To DS, Intra DS, Established, Sent To, and Unknown (Figure 7).
Basic configuration tweaking
You'll want to change your kismet.conf options depending on how you are using Kismet. If you are searching for APs, for example, you'll have channelhop = true set, at a minimum, and perhaps some finer-grained tweaks as well. If you are focusing exclusively on a single AP and want all the traffic you can get from it, you'll turn channel hopping off so as not to miss packets while scanning other channels. This can be useful for intrusion detection, since you'll want to track all clients attempting to or actually associating with the AP.
By default, Kismet writes its logs the to the directory it is started in. You can change this behavior with the logtemplate directive in kismet.conf. Unless you modify the logtypes directive in kismet.conf, Kismet will create dump, network, csv, xml, weak, cisco, and gps logs. The dump log contains raw packets and is suitable as input to other packet analyser programs, such as Aircrack-ng or Wireshark, the network protocol analyzer once known as Ethereal.
Conclusion
Kismet is a difficult to use for a noobie. You can't just install it and go and get any sort of meaningful results. It has to be properly configured, and properly configuring it may require that you learn more about wireless networking, hardware, and wireless security than you already knew. But the good news is that if you suffer through that pain, and learn more about those things, you'll find it worthwhile, because the more you know, they more it can do for you.
Kismet is capable of a lot more than I've covered here. The more you know about wireless and wireless security, the more of Kismet's feature list you can use, including things like decloaking hidden SSID networks and creating graphical representations of wireless networks.
But even at my relatively low level of wireless security knowledge, Kismet provides me with an important safeguard for wireless access to my home office LAN. I've already learned a lot more about wireless insecurity than I knew when I started. In particular, I've learned why not to rely on WEP to protect confidential data or communications, and how to detect unauthorized wireless access on my APs. All of which points to an additional important feature not noted in the documetation: Kismet is a great learning tool.